The Dark Side of Connectivity: Unveiling the Reality of Wi-Fi Hacking
Introduction
Welcome to the dark side of connectivity, where the reality of Wi-Fi hacking unveils itself. In today's rapidly advancing technological era, the importance of Wi-Fi cannot be underestimated. From homes to offices, coffee shops to airports, Wi-Fi has become an integral part of our everyday lives. However, with every convenience comes a potential risk, and Wi-Fi hacking has emerged as a serious concern.
 |
| The Dark Side of Connectivity: Unveiling the Reality of Wi-Fi Hacking |
Wi-Fi hacking refers to the unauthorized access and exploitation of wireless networks. Hackers, with malicious intent, target vulnerable Wi-Fi networks to gain unauthorized access to personal information, steal sensitive data, and cause havoc for unsuspecting users. The consequences of such attacks can be devastating, ranging from identity theft and financial loss to privacy breaches and compromised personal safety.
To carry out their malicious activities, hackers employ a variety of techniques. Exploiting weak passwords and default settings is a common method used to gain access to Wi-Fi networks. Additionally, techniques like sniffing, spoofing, and packet injection allow hackers to intercept and manipulate data packets, bypassing encryption measures.
There are different types of Wi-Fi attacks, with Man-in-the-Middle (MITM) attacks being one of the most common. In MITM attacks, hackers position themselves between the user and the target network, eavesdropping on communications and stealing sensitive information. Another type of attack is the Evil Twin attack, where hackers set up rogue access points that mimic legitimate networks, tricking users into connecting and compromising their data.
To carry out these attacks, hackers use specialized tools and software. Wireless network scanners and analyzers help identify vulnerable networks, while password cracking tools and keyloggers assist in bypassing security measures and gathering passwords.
Protecting your Wi-Fi network is of utmost importance in today's digital landscape. Creating strong passwords, changing default settings, implementing encryption protocols, and adopting secure configurations are crucial steps to safeguard against Wi-Fi hacking.
In conclusion, awareness and prevention are key in combating Wi-Fi hacking. By understanding the potential risks, staying informed about common techniques, utilizing protective measures, and regularly updating security protocols, you can secure your Wi-Fi network and minimize the threat of falling victim to malicious attacks. Stay vigilant and protect your connectivity.
Definition and significance of Wi-Fi hacking

The significance of Wi-Fi hacking lies in the potential risks and consequences it poses to individuals and organizations. Hackers can use Wi-Fi hacking techniques to intercept and manipulate data packets, bypass encryption measures, and gain access to sensitive information such as login credentials, financial data, and personal details. The consequences of such attacks can be devastating, ranging from identity theft and financial loss to privacy breaches and compromised personal safety.
Furthermore, Wi-Fi hacking can have severe implications for businesses and organizations. A successful Wi-Fi hack can lead to the theft of valuable intellectual property, customer data breaches, and reputational damage. The financial and legal ramifications can be enormous, affecting the trust and confidence of customers and stakeholders.
It is imperative to understand the definition and significance of Wi-Fi hacking in order to take proactive measures to protect our Wi-Fi networks and personal information. By being aware of the potential risks, staying informed about common hacking techniques, and implementing strong security protocols, individuals and organizations can minimize the threat of Wi-Fi hacking and safeguard their digital assets.
Potential risks and consequences of Wi-Fi hacking

- Identity theft: Wi-Fi hackers can intercept and manipulate data packets, enabling them to steal personal information such as usernames, passwords, and financial details. This information can then be used for identity theft, leading to financial loss and damage to one's reputation.
- Financial loss: Wi-Fi hacking can result in financial loss for individuals and businesses. Hackers can gain access to bank accounts, credit card information, and other financial data, allowing them to make unauthorized transactions and drain funds.
- Privacy breaches: Wi-Fi hacking compromises the privacy of individuals and organizations. Hackers can infiltrate networks and access sensitive files, photos, and documents. This invasion of privacy can lead to personal and professional consequences and even blackmail.
- Compromised personal safety: Wi-Fi hacking can have severe implications for personal safety. By gaining control of smart home devices or security systems connected to the Wi-Fi network, hackers can invade privacy, monitor activities, and pose physical threats.
- Reputational damage: For businesses and organizations, a Wi-Fi hack can lead to reputational damage. Customer confidence can be shattered, leading to a loss of trust and potential financial implications. Rebuilding a tarnished reputation may be a long and expensive process.
- Legal ramifications: Wi-Fi hacking is illegal and carries severe legal consequences. Engaging in such activities can result in criminal charges, fines, and imprisonment.
To mitigate these risks, individuals and organizations must take proactive measures to protect their Wi-Fi networks. Implementing strong security protocols, regularly updating firmware, using encrypted connections, and educating Wi-Fi users about potential threats are essential steps in safeguarding against Wi-Fi hacking.
Common Techniques Used in Wi-Fi Hacking

- Exploiting weak passwords and default settings: Hackers often target Wi-Fi networks that have weak passwords or still use default administrator credentials. By using password-cracking tools or guessing common passwords, they can easily gain unauthorized access.
- Sniffing, spoofing, and packet injection: Wi-Fi hackers use specialized software and hardware to intercept and manipulate wireless packets. This allows them to sniff network traffic, spoof MAC addresses, or inject malicious packets into the network, compromising its security.
- Social engineering and phishing attacks: Hackers rely on human vulnerabilities to gain access to Wi-Fi networks. They may impersonate legitimate organizations or individuals through phishing emails, text messages, or phone calls to trick users into revealing their Wi-Fi network credentials.
- Exploiting network vulnerabilities: Wi-Fi networks may have vulnerabilities in their encryption protocols or firmware that hackers can exploit. By identifying and exploiting these weaknesses, hackers can gain unauthorized access to the network.
- Rogue access points and evil twin attacks: Hackers set up rogue access points that mimic legitimate networks, tricking users into connecting to them. Once connected, the hacker can intercept network traffic and gain unauthorized access to sensitive information.
Protecting against these techniques requires implementing strong security measures such as using complex passwords, regularly updating firmware, and educating Wi-Fi users about the risks and best practices. Additionally, using encryption protocols such as WPA3 and secure configurations like disabling WPS can further enhance network security. Stay vigilant and ensure you are taking the necessary steps to safeguard your Wi-Fi network against these common hacking techniques.
Exploiting weak passwords and default settings

When it comes to passwords, using weak and predictable combinations such as "password" or "123456" makes it incredibly easy for hackers to crack them. They can use password-cracking tools or simply guess common passwords to gain access. Additionally, many users neglect to change the default passwords on their Wi-Fi routers or other network devices. Hackers are well aware of this and can easily exploit this oversight.
To protect your Wi-Fi network against these attacks, it is crucial to use strong and unique passwords. Make sure to include a combination of upper and lowercase letters, numbers, and special characters. Avoid using common words or personal information that can easily be guessed. Additionally, change the default administrator credentials on your Wi-Fi router or network devices to something unique.
Regularly updating your passwords and keeping them secure is equally important. Enable two-factor authentication whenever possible to add an extra layer of security. Educate your users about the importance of strong passwords and default setting changes to minimize the risk of falling victim to Wi-Fi hacking.
By addressing these weak areas, you can significantly strengthen the security of your Wi-Fi network and reduce the risk of unauthorized access.
Sniffing, spoofing, and packet injection
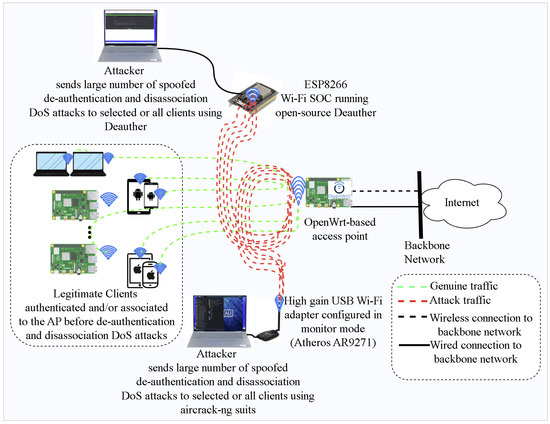
Sniffing involves capturing and analyzing network traffic to extract valuable information, including usernames, passwords, and other confidential data. Hackers can use specialized tools to capture data packets and then analyze them to uncover vulnerabilities or extract sensitive information.
Spoofing, on the other hand, refers to the act of impersonating a trusted entity, such as a Wi-Fi network or a website, to deceive users into providing their login credentials or other sensitive information. By creating fake access points or websites that mimic legitimate ones, hackers can trick users into connecting to their malicious network and steal their credentials.
Packet injection is a technique where hackers inject malicious data packets into a Wi-Fi network to disrupt or manipulate the communication between devices. This can lead to denial-of-service attacks, interception of sensitive data, or the injection of malicious code into connected devices.
To protect your Wi-Fi network against these techniques, it is crucial to implement strong encryption protocols, such as WPA2 or WPA3, which encrypt the data being transmitted over the network. Additionally, using a virtual private network (VPN) can add an extra layer of security by encrypting all your internet traffic and making it harder for hackers to intercept.
Moreover, regularly updating your devices' firmware and using up-to-date security patches can help mitigate the risk of exploits related to sniffing, spoofing, and packet injection. It is also advisable to use intrusion detection systems (IDS) or intrusion prevention systems (IPS) to detect and prevent suspicious activities on your network.
By implementing these measures, you can significantly reduce the risk of falling victim to sniffing, spoofing, and packet injection attacks and safeguard your Wi-Fi network from unauthorized access.
Types of Wi-Fi Attacks
- Man-in-the-Middle (MITM) attacks: In this type of attack, hackers intercept and potentially alter communication between two parties without their knowledge. By placing themselves between a user and a legitimate Wi-Fi network, the attacker can eavesdrop on sensitive information, such as login credentials or financial data. MITM attacks often involve techniques like ARP spoofing, where the attacker impersonates a network device to intercept and redirect traffic.
- Evil Twin attacks and rogue access points: In an Evil Twin attack, hackers create a fake wireless network that appears to be legitimate. The attacker sets up a rogue access point with a similar name and password as a trusted network, tricking unsuspecting users into connecting to their malicious network. Once connected, the hacker can monitor the user's activities or prompt them to enter sensitive information.
These attacks can have serious consequences, including identity theft, financial loss, and unauthorized access to personal and business data. To protect against these attacks, it is essential to regularly update your Wi-Fi network firmware, use strong encryption protocols, and be cautious when connecting to public networks. Additionally, employing intrusion detection systems (IDS) or intrusion prevention systems (IPS) can help identify and prevent these attacks from occurring on your network.
By staying informed about these types of attacks and implementing proactive security measures, you can significantly reduce the risk of falling victim to Wi-Fi hacking and ensure the safety of your network and data.
Man-in-the-Middle (MITM) attacks

The process of executing a MITM attack often involves techniques like ARP spoofing, where the attacker impersonates a network device and intercepts and redirects network traffic. This allows the hacker to gain access to critical data, such as login credentials, financial information, and personal details. The unsuspecting user remains clueless as their confidential information is surreptitiously captured by the attacker.
MITM attacks can have severe repercussions, including identity theft, financial loss, and unauthorized access to personal and business data. Such attacks are particularly prevalent on unsecured public Wi-Fi networks, where users unknowingly expose themselves to cybercriminals.
To protect against MITM attacks, it is crucial to take proactive measures. Ensure that your Wi-Fi network is secured with strong encryption protocols like WPA2 or WPA3. Regularly update your network firmware to patch any known vulnerabilities. Additionally, be cautious when connecting to public networks, as these are often prime targets for MITM attacks. Consider using a virtual private network (VPN) to encrypt your internet traffic and protect against eavesdropping.
By staying vigilant and implementing security measures, you can mitigate the risk of falling victim to Man-in-the-Middle attacks, thus safeguarding your sensitive information and preserving the integrity of your Wi-Fi network.
Evil Twin attacks and rogue access points

Rogue access points, on the other hand, are unauthorized access points that are installed on a network without the knowledge or permission of the network administrator. These access points can be used by hackers to intercept and manipulate network traffic, allowing them to capture valuable data or inject malicious code.
Both Evil Twin attacks and rogue access points exploit the trust that users have in their Wi-Fi networks. By creating a false sense of security, hackers can trick users into connecting to their malicious networks, compromising their personal and financial information.
Protecting your Wi-Fi network from these attacks requires a proactive approach. Here are some steps you can take:
- Always verify the legitimacy of Wi-Fi networks before connecting, especially in public places.
- Disable automatic Wi-Fi connections on your devices to prevent them from connecting to unauthorized networks.
- Regularly monitor your network for any unauthorized access points and promptly disable them.
- Use a strong encryption protocol like WPA2 or WPA3 to secure your network.
- Regularly update your Wi-Fi router’s firmware to patch any vulnerabilities.
By being cautious and implementing these security measures, you can significantly reduce the risk of falling victim to Evil Twin attacks and rogue access points, ensuring the safety of your Wi-Fi network and personal information.
References:
- Shell, J. (2019). The Art of Hacking WiFi: Evil Twin and Rogue Access Points. Retrieved from https://www.securedgenetworks.com/blog/the-art-of-hacking-wifi-evil-twin-and-rogue-access-points
Tools and Software Used in Wi-Fi Hacking

- Wireless network scanners and analyzers: Tools like Wireshark and Airodump-ng allow hackers to capture and analyze network traffic. They can identify vulnerable networks, monitor network activity, and capture sensitive information such as usernames and passwords.
- Password cracking tools: Tools like Aircrack-ng and Hashcat are used to crack Wi-Fi passwords. They use various techniques such as brute-force attacks, dictionary attacks, and rainbow table attacks to guess the password and gain access to the network.
- Keyloggers: Keyloggers are software programs or devices that record keystrokes on a computer or mobile device. In a Wi-Fi hacking scenario, keyloggers can be used to capture usernames, passwords, and other sensitive information as they are being entered by users.
- Rogue access point creation tools: Hackers can use tools like Karma and Jasager to create rogue access points. These tools trick devices into connecting to them by impersonating legitimate Wi-Fi networks. Once connected, the hacker can intercept and manipulate network traffic.
It is important to note that these tools are meant for educational and security research purposes, but they can also be misused by malicious individuals. As a network administrator or user, it is crucial to be aware of these tools and take necessary measures to protect your Wi-Fi network against them.
Wireless network scanners and analyzers

Using a wireless network scanner, hackers can search for available networks, gather information about them, and identify networks with weak security settings. They can then target these vulnerable networks for potential attacks.
Once the target network is identified, the hacker can utilize an analyzer tool to monitor network activity and capture packets of data. This allows them to analyze the network traffic, identify patterns, and extract sensitive information exchanged within the network.
Hackers can also use these tools to perform denial-of-service attacks by flooding the network with excessive traffic, resulting in network disruption and potential unauthorized access.
To protect your Wi-Fi network from these scanning and analyzing tools, it is crucial to implement strong security measures. This includes using strong passwords, regularly updating your network equipment's firmware, and utilizing encryption protocols such as WPA2.
Additionally, monitoring your network for any suspicious activity and regularly conducting security audits can help detect any potential vulnerabilities and prevent unauthorized access to your network.
By being aware of the tools and techniques used by hackers, you can take proactive steps to safeguard your Wi-Fi network and protect your sensitive information from falling into the wrong hands.
Password cracking tools and keyloggers

Password cracking tools:
These tools are designed to guess or crack the password of a Wi-Fi network by systematically trying various combinations of characters until the correct password is found. Some popular password cracking tools used by hackers include:
- Hydra: This tool uses brute force and dictionary attacks to guess passwords by trying various combinations.
- John the Ripper: This tool is known for its fast password cracking capabilities and supports multiple encryption algorithms.
- Hashcat: It is a powerful password cracking tool that can crack passwords by using GPUs for faster processing.
Keyloggers:
Keyloggers are malicious software or hardware devices that record keystrokes, allowing hackers to capture sensitive information such as usernames and passwords. There are two types of keyloggers:
- Software keyloggers: These are installed on a victim's device without their knowledge and silently record all keystrokes. They can be delivered through malicious email attachments or infected websites.
- Hardware keyloggers: These devices are physically plugged between the keyboard and the computer and record all keystrokes. They are difficult to detect and require physical access to the victim's device.
To protect your Wi-Fi network from password cracking tools and keyloggers, it is important to follow these measures:
- Use strong, unique passwords that include a combination of uppercase and lowercase letters, numbers, and symbols.
- Regularly update your Wi-Fi router's firmware to patch any known vulnerabilities.
- Install and update reliable antivirus software to detect and remove keyloggers from your devices.
- Be cautious when clicking on suspicious links or downloading files from unknown sources.
By implementing these security measures, you can significantly reduce the risk of falling victim to password cracking tools and keyloggers and keep your Wi-Fi network and sensitive information secure.
Protecting Your Wi-Fi Network

- Creating strong passwords and changing default settings: One of the most effective ways to secure your Wi-Fi network is by creating strong passwords. Use a combination of uppercase and lowercase letters, numbers, and symbols to make it harder for hackers to guess. Additionally, change the default SSID (network name) and password that came with your router, as these are often easily available to attackers.
- Implementing encryption protocols and secure configurations: Enable WPA2 (Wi-Fi Protected Access 2) encryption on your router, as it provides stronger security than older encryption standards. Additionally, disable remote administration and UPnP (Universal Plug and Play) features on your router, as these can potentially be exploited by hackers.
- Regularly updating firmware: Keep your Wi-Fi router's firmware up-to-date by checking for and installing any available updates. Manufacturers often release firmware updates to patch known vulnerabilities, and by staying updated, you can protect your network from potential risks.
- Enabling network segmentation and guest networks: If your router supports it, consider implementing network segmentation to separate your devices into different subnets. This can help limit the impact of a potential breach. Additionally, enabling a guest network allows guests to access the internet without gaining access to your main network and its sensitive data.
- Monitoring and logging network activity: Regularly monitor your network for any suspicious activity and enable logging to keep a record of network traffic. This can help you identify any potential attacks or breaches and take appropriate actions.
Remember, Wi-Fi network security is an ongoing process. Stay updated on the latest security practices and regularly review and update your security measures to ensure the continued protection of your network and data.
Creating strong passwords and changing default settings

When it comes to passwords, it is essential to create a strong and unique one. Avoid using common words or personal information that can be easily guessed by hackers. Instead, opt for a combination of uppercase and lowercase letters, numbers, and symbols. The longer and more complex your password is, the more secure it will be.
In addition to strong passwords, it is crucial to change the default settings that came with your router. Attackers often know the default settings, making it easier for them to gain access to your network. Change the default SSID (network name) and the password as soon as possible. Choose a unique network name that does not reveal any personal information.
Regularly changing passwords and updating the router's settings can help ensure that you stay one step ahead of potential hackers. It is recommended to change passwords at least every three months, and whenever there are changes in network personnel or the addition of new devices.
By creating strong passwords and changing default settings, you are fortifying the first line of defense for your Wi-Fi network. These simple yet effective measures can go a long way in protecting your network and keeping your sensitive information secure.
Implementing encryption protocols and secure configurations
- Enable WPA2 or WPA3 encryption: The use of strong encryption protocols, such as Wi-Fi Protected Access 2 (WPA2) or the newer WPA3, is crucial in securing your network. These encryption standards encrypt the data transmitted over your network, making it much harder for attackers to intercept and decipher.
- Disable WPS (Wi-Fi Protected Setup): WPS is a convenient feature that allows for quick and easy device connectivity. However, it can also be a security vulnerability. It is recommended to disable WPS, as it can be exploited by hackers to gain unauthorized access to your network.
- Implement MAC address filtering: MAC address filtering allows you to specify which devices are allowed to connect to your network based on their unique MAC addresses. By configuring your router to only accept connections from trusted MAC addresses, you can prevent unauthorized devices from accessing your network.
- Regularly update firmware: Keeping your router's firmware up to date is essential, as it ensures that you have the latest security patches and fixes for any vulnerabilities. Check your router manufacturer's website regularly for firmware updates and install them promptly.
- Enable a firewall: A firewall acts as a barrier between your network and the outside world, monitoring and filtering incoming and outgoing network traffic. Enabling a firewall on your router adds an extra layer of protection against unauthorized access and potentially malicious attacks.
- Disable remote access: Remote access functionality allows you to manage your router settings from outside your network. However, it can also be exploited by hackers. Disable remote access unless absolutely necessary, and if required, ensure that strong authentication measures are in place.
By implementing encryption protocols like WPA2/WPA3, disabling vulnerable features like WPS, and following secure configuration practices, you can significantly strengthen the security of your Wi-Fi network, safeguarding your data and protecting against potential attacks.
Conclusion

By understanding the common techniques used in Wi-Fi hacking, such as exploiting weak passwords and default settings, as well as sniffing and spoofing attacks, you can better identify and mitigate these risks. Additionally, being aware of the different types of Wi-Fi attacks, such as Man-in-the-Middle attacks and Evil Twin attacks, will allow you to implement appropriate security measures.
Using tools and software like wireless network scanners and analyzers can help you monitor your network for any suspicious activity, while password cracking tools and keyloggers can be used to test the strength of your passwords and identify vulnerabilities.
To protect your Wi-Fi network, it is crucial to create strong passwords, change default settings, and implement encryption protocols like WPA2 or WPA3. Furthermore, configuring your router to disable vulnerable features like WPS, implementing MAC address filtering, regularly updating firmware, enabling a firewall, and disabling remote access are essential steps in enhancing your network's security.
By taking these preventive measures, you can minimize the risk of Wi-Fi hacking and ensure the confidentiality and integrity of your data. Stay informed, stay vigilant, and protect your Wi-Fi network from potential attacks.
Awareness and prevention tips for safeguarding against Wi-Fi hacking

- Stay updated: Keep yourself informed about the latest Wi-Fi hacking techniques and vulnerabilities. Stay abreast of security news and updates to ensure you are aware of any potential threats.
- Use strong passwords: Create unique and strong passwords for your Wi-Fi network, router, and other devices connected to it. Use a combination of letters, numbers, and special characters, and avoid common or easily guessable passwords.
- Change default settings: Change the default login credentials and other settings of your router to make it more difficult for hackers to gain unauthorized access. Disable remote administration and change the default SSID (network name) to avoid being targeted.
- Enable encryption: Implement encryption protocols like WPA2 or the newer WPA3 to secure your Wi-Fi network. Encryption scrambles the data sent over your network, making it much harder for hackers to intercept and decipher.
- Enable MAC address filtering: Restrict access to your Wi-Fi network by allowing only specific devices with registered MAC addresses to connect. This adds an extra layer of protection against unauthorized devices.
- Keep firmware updated: Regularly update the firmware of your router to ensure you have the latest security patches and bug fixes. Check the manufacturer's website periodically for updates, or enable automatic updates if available.
- Use a firewall: Enable the built-in firewall on your router to prevent unauthorized access and filter out potentially malicious traffic.
By following these awareness and prevention tips, you can significantly reduce the risk of Wi-Fi hacking and protect the security and privacy of your network. Stay vigilant and take proactive steps to safeguard your Wi-Fi network from potential threats.
Frequently Asked Questions

A: Wi-Fi hacking refers to the unauthorized access, manipulation, or interception of wireless networks. It involves exploiting vulnerabilities in Wi-Fi systems to gain access to sensitive information, disrupt network operations, or launch malicious activities.
Q: What are the risks of Wi-Fi hacking?
A: Wi-Fi hacking poses several risks, including identity theft, data breaches, financial loss, and privacy invasion. Hackers can intercept your communications, steal personal information, install malware on connected devices, or even use your network for illegal activities, leaving you vulnerable to legal consequences.
Q: How can I protect my Wi-Fi network from hacking?
A: To protect your Wi-Fi network, you should follow these preventive measures:
- Create strong and unique passwords for your Wi-Fi network, router, and connected devices.
- Change default router login credentials and settings to prevent easy access by hackers.
- Enable encryption protocols such as WPA2 or WPA3 to scramble data transmission and make it harder to intercept.
- Implement MAC address filtering to restrict access to authorized devices only.
- Keep your router firmware updated by regularly checking for manufacturer updates or enabling automatic updates.
- Enable a firewall on your router to filter out potentially malicious traffic.
Q: What tools do hackers use for Wi-Fi hacking?
A: Hackers use various tools, such as wireless network scanners and analyzers to identify vulnerable networks, password cracking tools to decipher weak passwords, and keyloggers to capture keystrokes and obtain login credentials. These tools help them exploit security weaknesses in Wi-Fi networks.
Q: How can I stay informed about Wi-Fi hacking trends and techniques?
A: Stay updated with the latest news and security updates related to Wi-Fi hacking. Subscribe to reliable security blogs, follow cybersecurity professionals on social media, and participate in online forums to stay informed about emerging threats and preventive measures.
Remember, staying vigilant and implementing robust security measures is essential to safeguarding your Wi-Fi network from hacking attempts.











